This week is all about creating awareness. Creating awareness for the configuration options that are available for Microsoft Edge via the Microsoft 365 admin center, also known as the Microsoft Edge management service. The Microsoft Edge management service is an alternative method, besides Microsoft Intune, for configuring the Microsoft Edge browser via the Cloud. The configurations are stored in the Cloud and the settings can be applied through a group assignment. The user must be signed into the browser to receive those settings, and the browser must be restarted to make new settings applicable. So, pretty similar to the capabilities within Microsoft Intune. Besides that, the Microsoft Edge management service also provides access to additional settings, such as organization branding, AI, and specific security settings. And especially the latter contains some interesting settings that have a direct relation with Microsoft Intune and might directly impact the user. This post will provide a closer look at those specific security settings and the direct relation and integration with Microsoft Intune.
Note: Microsoft 365 admin center provides an overview of Edge configurations that are created via either method.
Configuring blocking other browsers
When looking at the different configuration options that are available via the Microsoft Edge management service, it gets pretty interesting. Especially when looking at the side-effect of those settings. There are now multiple settings and configuration options within the Microsoft Edge management service, such as the Microsoft Purview DLP settings, that refer to blocking other browser to get fully in control. Besides that, the Microsoft Edge management service also contains a specific setting that does something similar. The main thing to keep in mind is what it actually does in those cases.
Option 1: Apply Edge settings to all users to Activate Purview DLP policies in Microsoft Edge for Business
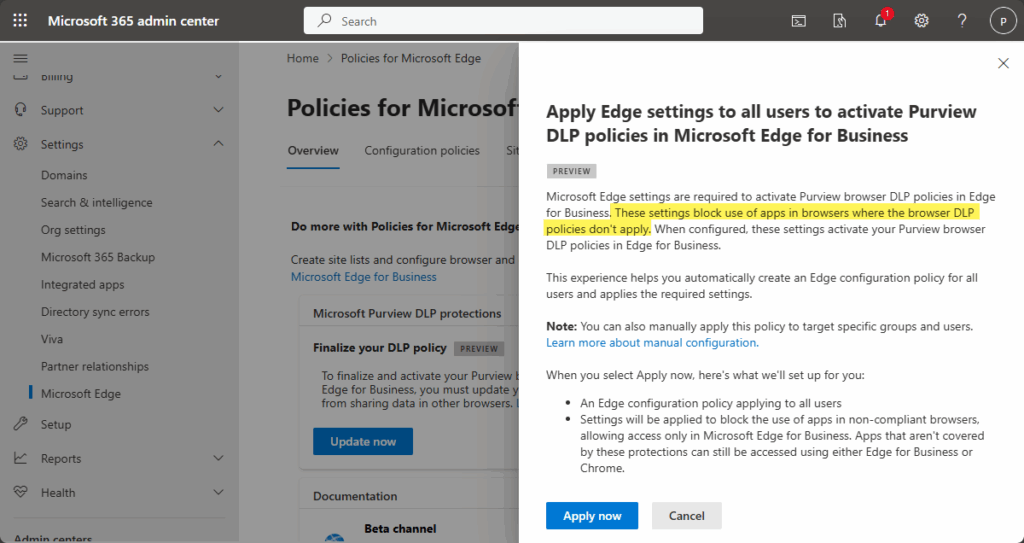
The first setting that is now often directly shown on the front of the page when navigating to Settings > Microsoft Edge, is the setting to finalize your DLP policy. That setting is shown below in Figure 1 and is focused on protecting corporate data by activating Purview browser DLP policies in Microsoft Edge for Business. And to make sure that users are forced into actually using Microsoft Edge for Business, that setting will also create some configurations within Microsoft Intune. Those configurations are focused on blocking any other browser that might be available. That behavior is achieved by implementing AppLocker policies.
Option 2: Block other browsers
The second setting is less prominent available, but triggers similar behavior. Every policy object within the Microsoft Edge management service, contains some additional configuration options. That is even applicable for policies that are created within Microsoft Intune. When selecting one of the policies in the Policies for Microsoft Edge section, there are actually three tabs available. Simply navigate to the Customizations Settings tab and select the Security settings category. That category contains the setting Block other browsers, as shown below in Figure 2, that does exactly what it says: it blocks other browsers. That behavior is also achieved by implementing AppLocker policies.

Result of the configuration options
When the different configuration options with the Microsoft Edge management service are being used, that might have a direct impact on the users within the environment. That impact is caused by the configurations that are created when using those options. As shown below in Figure 3 there are multiple policy objects that can get created in Microsoft Intune.
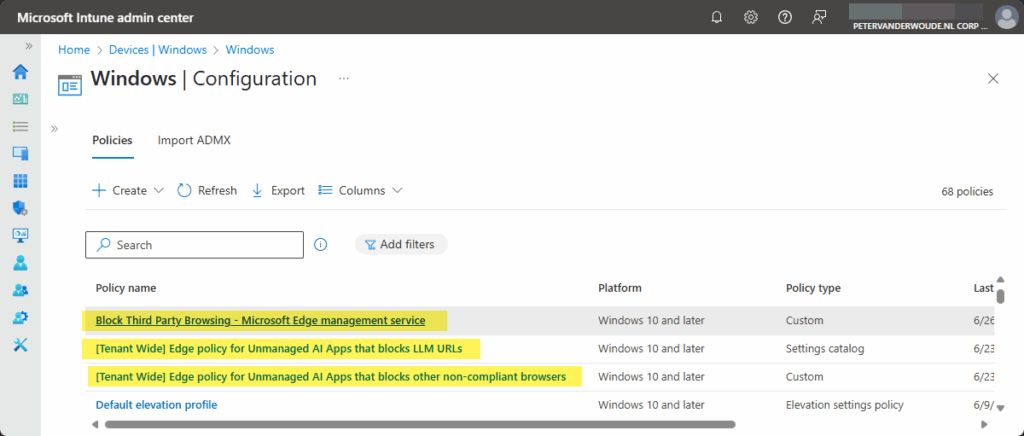
The policy objects [Tenant Wide] Edge policy for Unmanaged AI Apps that blocks other non-compliant browser and [Tenant Wide] Edge policy for Unmanaged AI Apps that blocks LLM URLs are created when using the first configuration option, and the policy object Block Third Party Browsing – Microsoft Edge management service is created when using the second configuration option. Both of the custom policies contain AppLocker configurations for blocking other browsers. A brief and clear snippet of such a configuration is shown below in Figure 4. That contains information about the service that initiated the configuration and the configuration itself, which clearly shows the link with AppLocker. It contain deny configurations for EXE and StoreApps of different browsers.
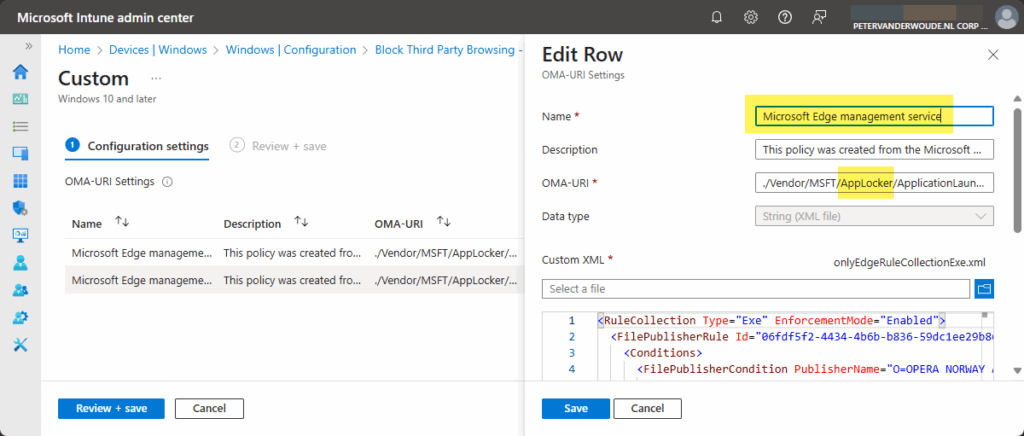
Note: The AppLocker policies contain deny rules for different browsers that are currently available. That includes Opera, Firefox, Brave, 360 Secure, Chrome, Vivaldi, Tor, Puffin, Yandex, UC, Wave.
Experiencing the behavior when blocking other browsers
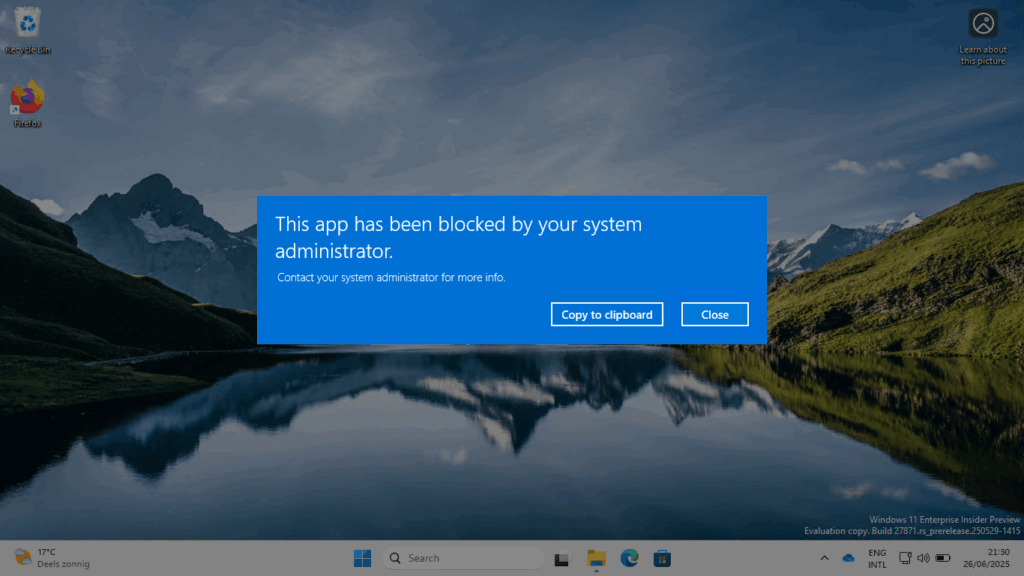
When the custom policies are created within Microsoft Intune, they are immediately applicable to the users. Simply because those custom polices are created including an assignment to All users. That makes it really important to be familiar with these custom policies and to understand the impact those custom policies. Basically, every configured browser will be blocked by AppLocker, as shown below in Figure 5. As soon as the users starts one of those browsers, the app will be blocked.
More information
For more information about blocking other browsers via Microsoft Edge policies, refer to the following docs.
- Get started with configuration policies | Microsoft Learn
- Set up Microsoft Purview DLP policies in the Edge management service | Microsoft Learn
- Protect Office documents with Microsoft Purview Information Protection labeling | Microsoft Learn
Discover more from All about Microsoft Intune
Subscribe to get the latest posts sent to your email.


I can’t see the option 2 – Option 2: Block other browsers
Do I need to enable anything?
Thank you.
Hi Rafel,
Not to my knowledge. You should just be able to select any policy in the Policies for Microsoft Edge section and navigate to the Customizations Settings tab. Or just create a new policy there.
Regards, Peter
Option 2: Block other browsers is actually unintuitive to find unless you know where it is.
You have to create a policy first and then go into it afterwards to get those options to show.
Here is the link to the correct URL: https://admin.cloud.microsoft/?Q=m365setup#/Edge/PolicyConfiguration
It seems most tenmant don’t have the Edge section yet, at first it seems bughy but after some times (30m to 1h) Microsoft Edge section should appear, under settings.
Than you can create a config, and inside thsi config you can change the security under Customization Settings Tab.
Thank you for sharing your experience Francois.
Regards, Peter
The correct way are :
1) create a custom OMA-URI config (Template, Custom)
2) Add those two OMA-URI:
./Vendor/MSFT/AppLocker/ApplicationLaunchRestrictions/MicrosoftEdgeManagement1/EXE/Policy
./Vendor/MSFT/AppLocker/ApplicationLaunchRestrictions/MicrosoftEdgeManagement2/StoreApps/Policy
And use XML string file.
Should be the best and recommand way to use only Edge browser.
Thank you for sharing, Francois. The main thing is that administrators should be familiar with the impact of the configurations that can be created.
Regards, Peter