This week is all about the preventing accidental device wipes by using multiple administrative approval in Microsoft Intune. Multiple administrative approval on itself is nothing new, but the latest addition to that functionality makes it a lot more powerful. Before, multiple administrative approval was mainly focused adding apps and scripts to Microsoft Intune. Nowadays, multiple administrative approval can also be used for Intune roles and the most critical device actions. Those device actions include device wipe, device retire, and device delete. With those device actions, there will be a little safety net for IT administrators when performing impactful device actions without really giving in on security. Multiple administrative approval will help with preventing accidentally wiping a device. Every device wipe will require an approval from another IT administrator, and only after that approval the action can be continued. This post will provide more information, the configuration, and the experience.
Creating an access policy for device wipe
When looking at multiple administrative approval, it always starts with an access policy. The access policy is used to specify the profile types that are protected – in this case the device wipe action – and the Entra security group that contains the administrative users for the additional approval. After configuring that policy, any administrator account that is used to perform a device wipe will require an explicit approval from a different administrative account. On top of that, the configuration of that policy also nowadays already requires multiple administrative approval. The following six steps walk through the creation of the first stage of an access policy that is used to protect device wipes. Similar steps can be used to protect other profile types.
- Open Microsoft Intune admin center navigate to Tenant administration > Multi Admin Approval
- On the Tenant admin | Multi Admin Approval page, select Access policies
- On the Access policies tab, click Create
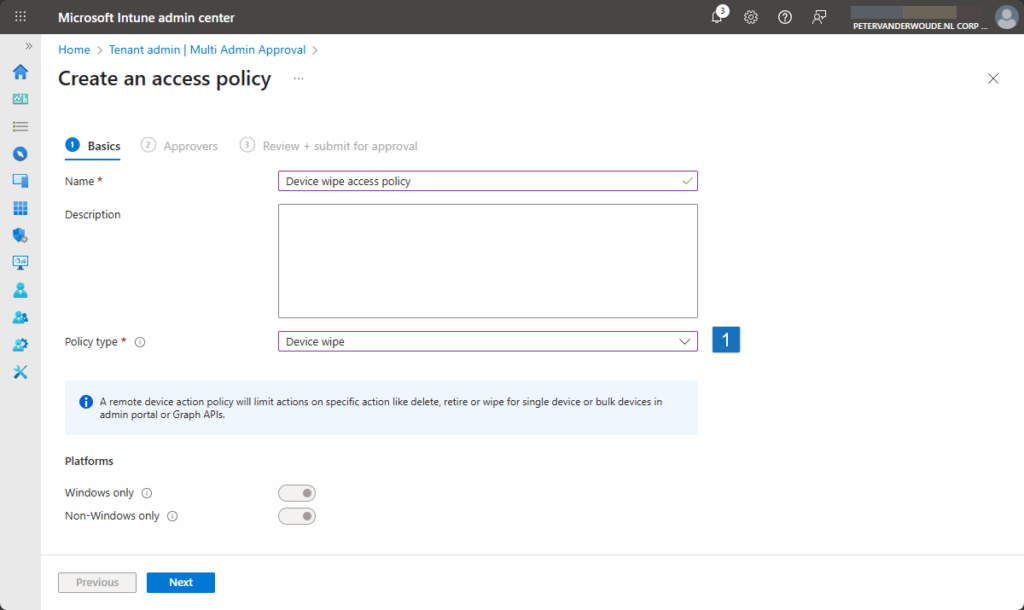
- On the Basics page, as shown below in Figure 1, provide the following information and click Create
- Name: Provide a name for the policy to distinguish it from other similar policies
- Description: (Optional) Provide a description for the policy to further differentiate policies
- Profile type: Select Device wipe to apply this policy only to the device wipe action
- On the Approvers page, click Add groups to select the Entra security group that contains the administrative accounts of the approvers and click Next
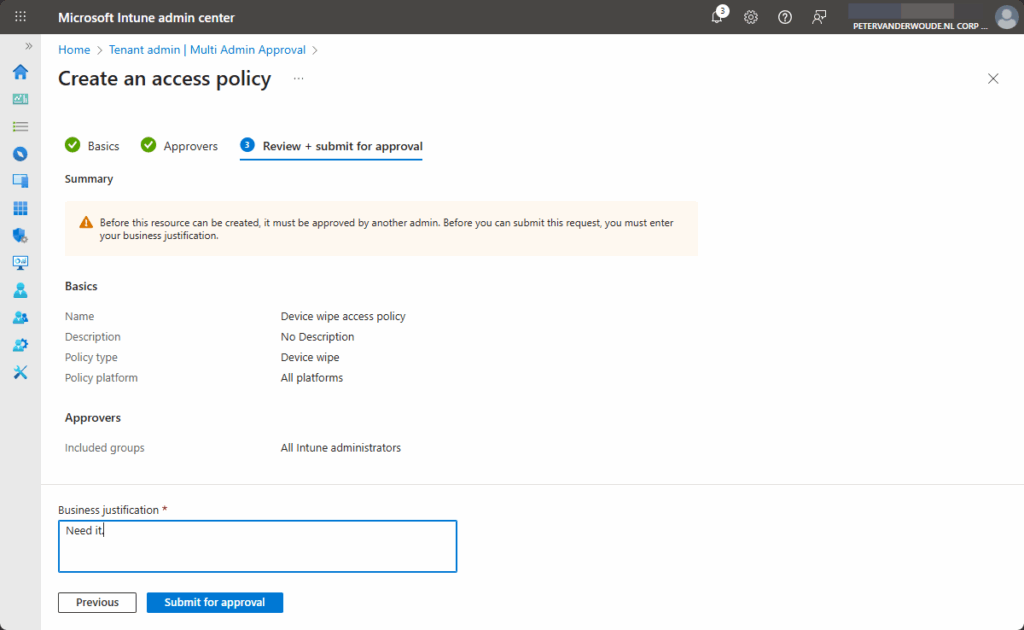
- On the Review + submit for approval page, as shown in Figure 2, review the configuration, specify a Business justification, and click Submit for approval
After submitting the access policy for approval, another administrator must approve the creation of the access policy. The following three steps walk through the approval for the creation of the access policy that is used to protect device wipes.
- Open Microsoft Intune admin center navigate to Tenant administration > Multi Admin Approval
- On the Tenant admin | Multi Admin Approval page, select All requests
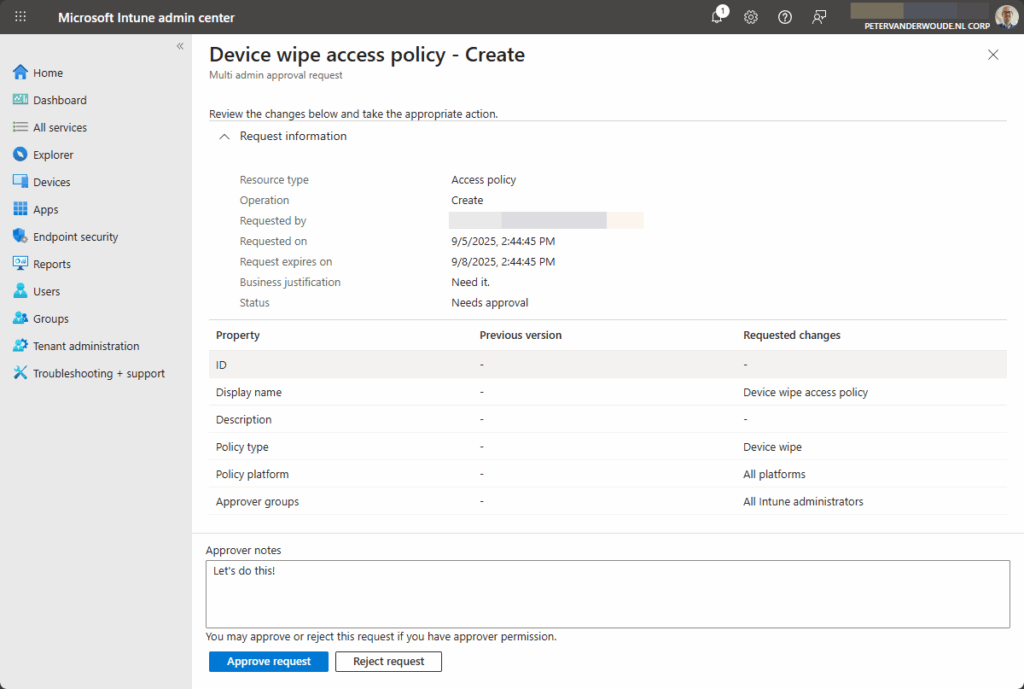
- On the Access policies tab, as shown in Figure 3, select the just created multi admin approval request for the new access policy, specify an Approver note and click Approve request
Once the access policy has been approved, the initial administrator can complete the creation of the access policy. The following three steps walk through the completing the creation of the access policy that is used to protect device wipes.
- Open Microsoft Intune admin center navigate to Tenant administration > Multi Admin Approval
- On the Tenant admin | Multi Admin Approval page, select All requests
- On the All requests tab, as shown in Figure 4, select the just approved multi admin approval request for the new access policy and click Complete request

Performing a device wipe
After creating the access policy for the device wipe action, the biggest change will be in the administrator experience when performing a device wipe action. In any scenario, a device wipe will require at least two administrators. An administrator performing the device wipe action, and an administrator approving the device wipe action. That directly translates to a different administrator experience. The following three steps walk through the changed process for performing a device wipe action.
- Open Microsoft Intune admin center navigate to Devices > All devices
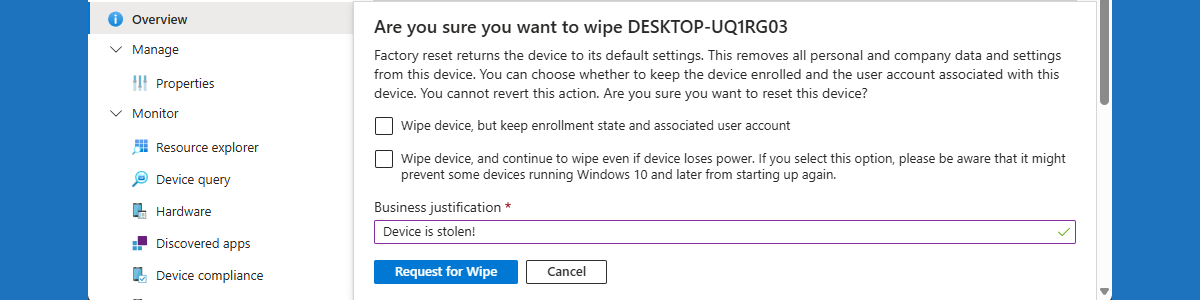
- On the Devices | All devices page, select the device that should be wiped and click Wipe
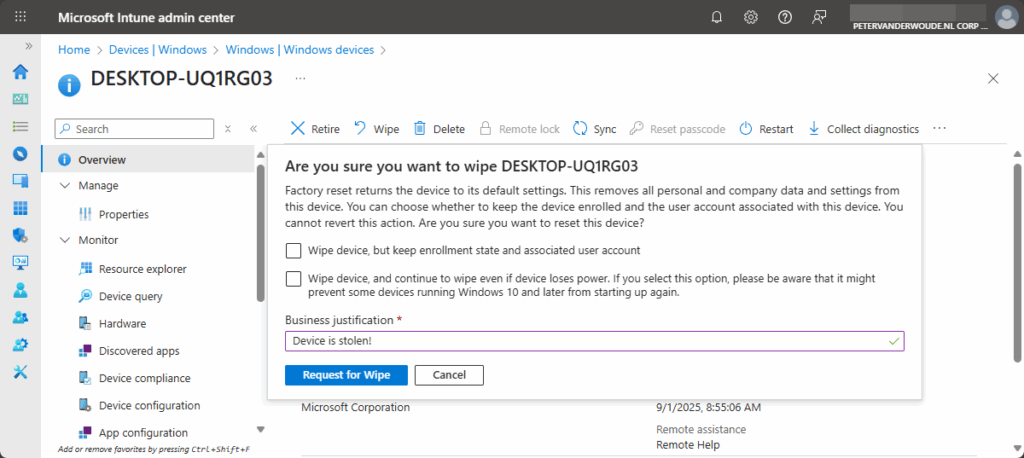
- On the Are you sure you want to wipe {device name} dialog box, as shown below in Figure 5, select the required boxes, provide a Business justification and click Request for Wipe
After submitting the device wipe action for approval, another administrator must approve that action. The following three steps walk through the approval of that device wipe action.
- Open Microsoft Intune admin center navigate to Tenant administration > Multi Admin Approval
- On the Tenant admin | Multi Admin Approval page, select All requests
- On the All requests tab, as shown in Figure 6, select the just created multi admin approval request for the device wipe action, specify an Approver note and click Approve request
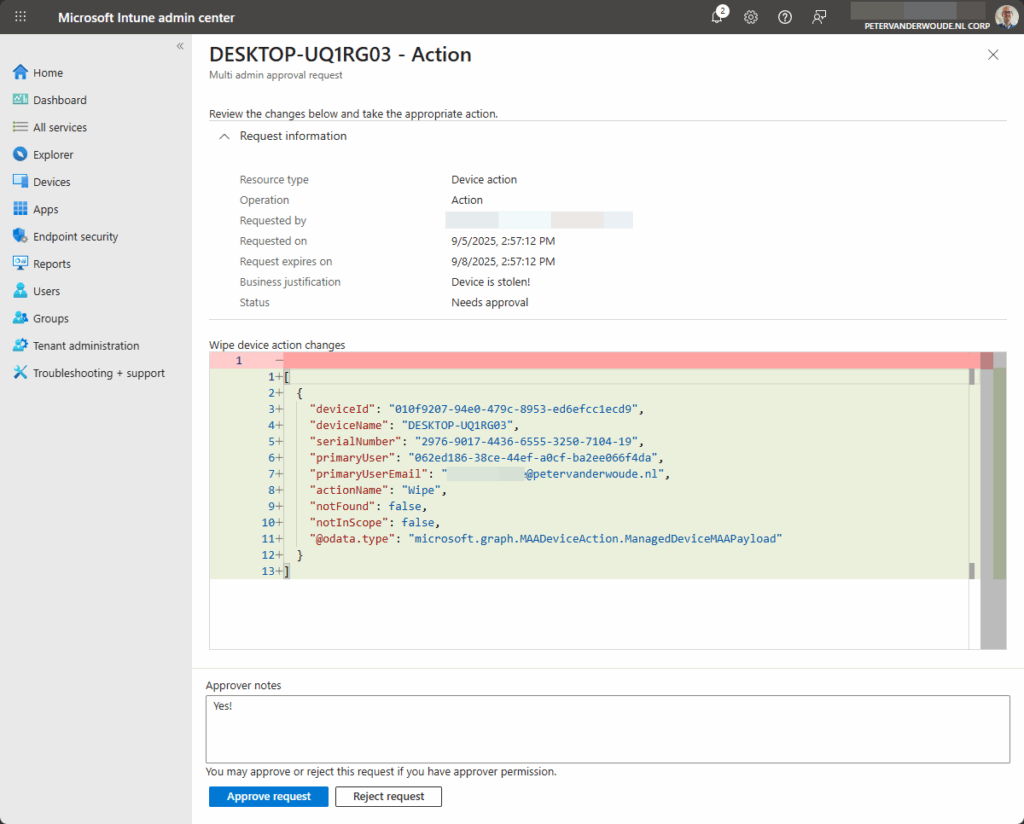
Once the device wipe action has been approved, the initial administrator can complete the action. The following three steps walk through the completion of performing the device wipe action.
- Open Microsoft Intune admin center navigate to Tenant administration > Multi Admin Approval
- On the Tenant admin | Multi Admin Approval page, select All requests
- On the Access policies tab, as shown in Figure 7, select the just approved multi admin approval request for the device wipe action and click Complete request
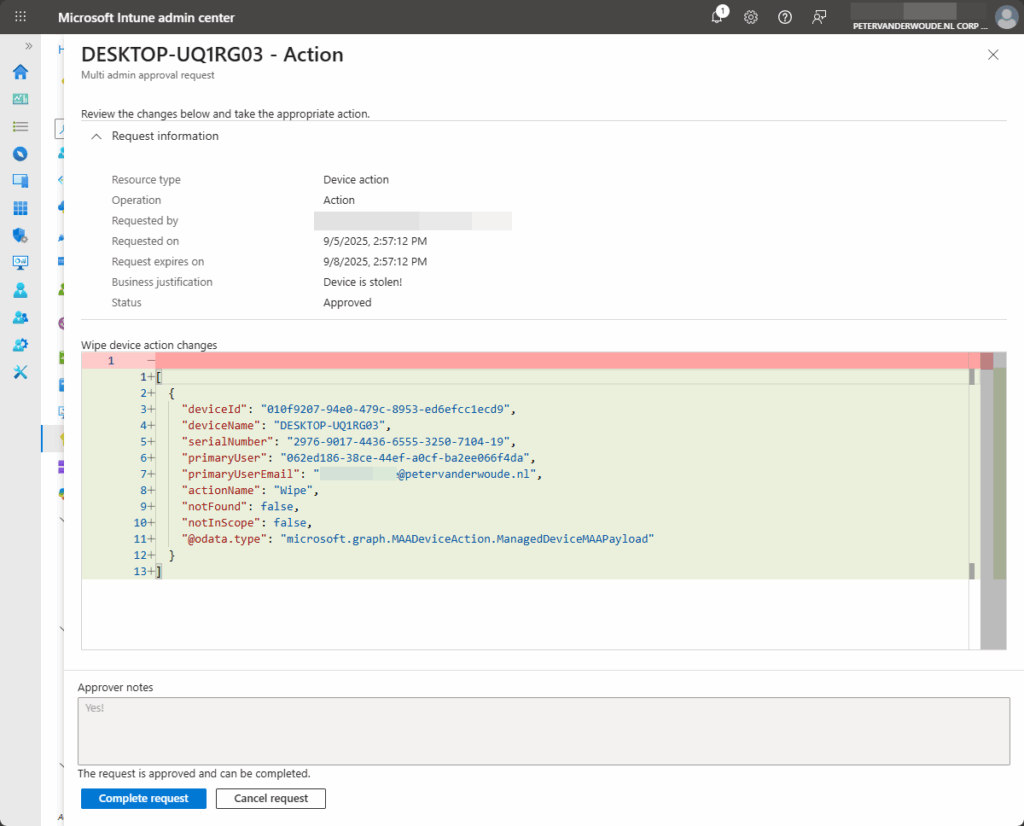
More information
For more information about multiple administrative approvals, refer to the following docs.
Discover more from All about Microsoft Intune
Subscribe to get the latest posts sent to your email.

Hi Peter, are there any plans to assign this feature to specific staff e.g. multiple approval for a junior IT admin who is still in training but not for Senior System Engineers, thanks – Gerry
Hi Gerry,
At this moment it is scoped on the functionality. Haven’t heard anything about plans to change that.
Regards, Peter
Thanks peter.