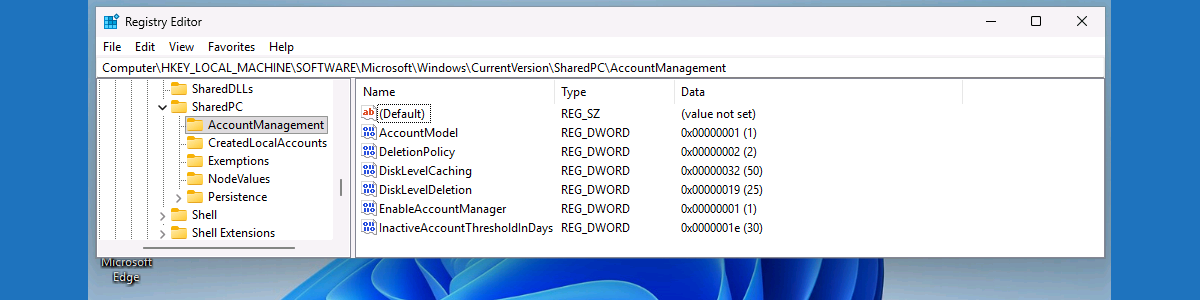
Managing account management on Shared PCs
This week is all about a closer look at Shared PC Mode on Windows 11. More specifically, this week is all about managing account management capabilities in Shared PC Mode. Account management in Shared PC Mode is about managing the accounts on the device, determining the users that can sign on to the device, and configuring what automatically starts. This post will mainly focus on the first, managing the accounts on the device. Especially on a device that is being shared between many users, it is important to make sure that those accounts are managed properly to prevent the disk from filling up completely. Luckily, within the capabilities of Shared PC Mode there are options for managing those accounts, including cleaning up accounts when needed. …