This week is all about the new ability to use a QR code to sign in to specific apps on (shared) Android devices. QR code authentication is a new authentication method in Entra that enables frontline workers to sign in to apps on shared devices. That authentication method provides users with the ability use a unique QR code in combination with a PIN to sign in. That eliminates the need for users to enter usernames and passwords, making it a more user-friendly experience on shared devices. On Android devices, QR code sign in is now available for the Managed Home Screen app, the Teams app, and even during the web sign-in. This post will briefly go through the QR code authentication method, directly followed with the configuration steps. This post will end with the enabling QR code authentication on shared Android devices and the related user experience.
Note: QR code authentication is currently only supported on iOS/iPadOS devices or Android devices.
Introducing QR code authentication
When looking at the QR code authentication method, it all starts with the primary use case: frontline workers. QR code authentication provides a simple authentication method that consists of a unique QR code and a numeric PIN. The QR code is unique to the user and is used as an identifier for the user. It can be downloaded and printed by using Microsoft Entra admin center, My Staff, or Microsoft Graph. The initial temporary numeric PIN is generated during the creation of the QR code, and is also shared with the user. The user has to change that PIN during the first sign-in. The PIN itself is bound to that specific QR code only. QR code authentication is seen as a single-factor authentication method, in which the PIN is a credential. The IT administrator can only configure the number of digits that are required for the PIN and the lifetime of the PIN. The complexity can not be configured. Due to simplicity of the authentication method, it should only be used for the primary use case.
It is strongly advised not to enable QR code authentication for all users within the organization. QR code authentication should only be used for specific users, on specific devices. Besides that, it’s important to actually limit the usage of QR code authentication, as it’s only a single-factor authentication method. That’s why it’s also important to limit its usage in combination with Conditional Access policies, as another layer of security. All with the focus of limiting the usage of QR code authentication on the shared devices for frontline workers. Think about setting limits on specific users, devices, and possibly even locations.
In case users forget to take their QR code, the IT administrator can generate a temporary QR code, with a short lifetime.
Enabling QR code authentication as an authentication method
After being familiar with the QR code authentication, it’s time to look at the configuration. The configuration starts with the authentication methods. The QR code authentication method should be enabled only for the specific frontline workers that will actually need to use it on shared devices. The following three steps walk through the process of enabling it.
- Open the Microsoft Entra admin center portal and navigate to Protection > Authentication methods
- On the Authentication methods | Policies page, navigate to Policies and select QR code (Preview)
- On the QR code (Preview) settings page, as shown below in Figure 1, configure at least the following and click Save
- On the Enable and Target tab, select Enable and configure the assigned users by using Select groups > Add groups
- On the Configure tab, configure the default for the QR PIN Length by selecting a number between 8 and 20 and for Lifetime of standard QR code (days) by selecting a number between 1 and 395

Creating a QR code authentication method for a user
When the QR code authentication method is available for the user, it’s time to look at creating QR codes. That can be achieved using either the Microsoft Entra admin center, My Staff, or Microsoft Graph API. The following three steps walk through the process of creating a QR code and PIN for a frontline workers.
- Open the Microsoft Entra admin center portal and navigate to Identity > All users
- On the Users page, select the specific user and select Authentication methods > Add authentication method
- On the Add authentication method blade, as shown below in Figure 2, configure the following information and click Add
- Choose method: Select QR code as the authentication method for the user
- Expiration: Specify the expiration date and time of the generated QR code
- Activation time: Specify the activation time of the QR code
- PIN: Specify the PIN manually or automatically generate the PIN

Note: After creating the QR code for a user, the QR code can no longer be accessed via the different portals and APIs.
Enabling the Microsoft Authenticator app for QR code authentication
When the QR code authentication method is available, it’s time to look at actually using it. On Android devices, QR code authentication is currently available for the Managed Home Screen app, the Teams app, and even during the web sign-in. For those sign-ins to be able to actually rely on a QR code, the Microsoft Authenticator must be configured. That can be achieved by using a app configuration policy for the Microsoft Authenticator app. Within that policy the Preferred authentication configuration (preferred_auth_config) configuration key must be configured with the value of qrpin. The following six steps walk through that specific configuration for the Microsoft Authenticator app.
- Open the Microsoft Intune admin center portal navigate to Apps > App configuration policies
- On the Apps | App configuration policies blade, click Add > Managed devices
- On the Basics page, provide the following information and click Next
- Name: Provide a valid name to distinguish the policy from other similar policies
- Description: (Optional) Provide a valid name to further distinguish the policy from other similar policies
- Device enrollment type: (Grayed out) Managed devices
- Platform: Select Android Enterprise
- Profile type: Select Fully Managed, Dedicated, and Corporate-Owned Work Profile Only
- Public apps: Select Select app > Microsoft Authenticator as the app to configure
- On the Settings page, provide at least the following information and click Next
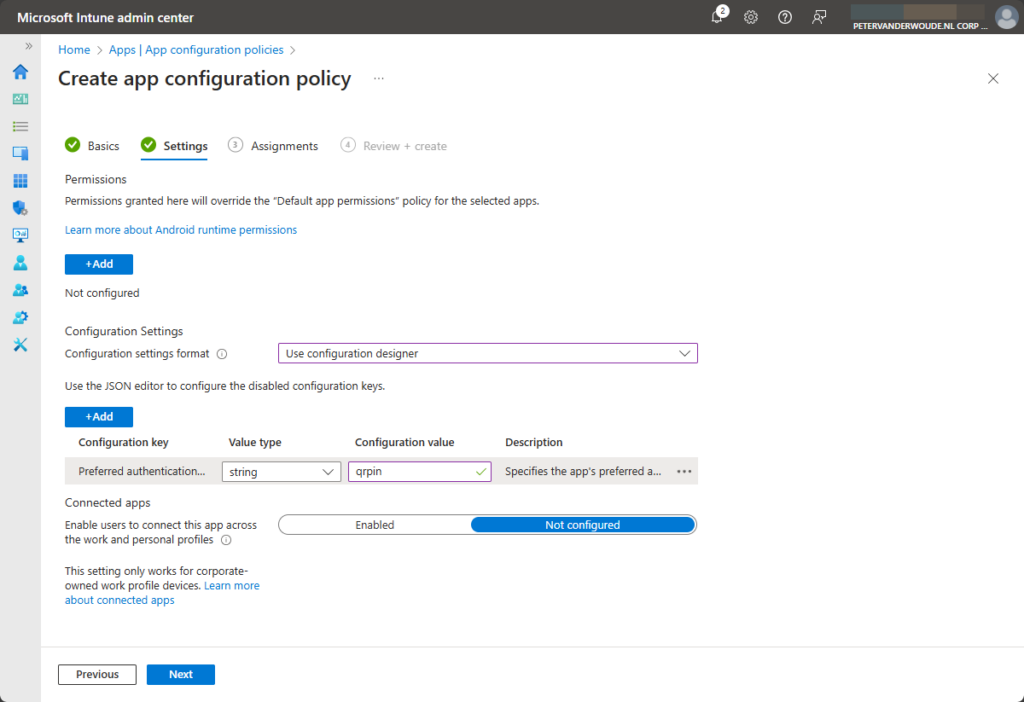
- On the Configuration settings section, as shown below in Figure 3, perform the following actions
- Configuration settings format: Select Use configuration designer
- Click Add to add the Preferred authentication configuration configuration key
- Select string as value type and specify qrpin as the configuration value
- On the Assignments page, configure the required assignment by selecting the applicable user group and click Next
- On the Review + create page, review the configuration and click Create
Note: Keep in mind that this configuration can also be used in combination with other app configurations.
Experiencing QR code authentication on Android apps
After all the required configurations are in place, and the user received their QR code, it’s time to experience the QR code sign in on the supported Android apps. For that it’s important the device is configured as a shared device, and preferably by using Entra shared device mode. That enables the user, when the Managed Home Screen is configured correctly, to directly sign in to the device by using the QR code sign in. When that is all in place, the user experience is pretty straight forward. The user starts the device and taps on Scan QR Code, as shown below in Figure 4. That enables the user to actually scan the received QR code, as shown below in Figure 5. After scanning the QR code the user is requested to enter their PIN, as shown below in Figure 6. During the initial sign in the user uses the temporary PIN that they’ve received, and the user will be requested to change the PIN.
More information
For more information about QR code authentication, refer to the following docs.
Discover more from All about Microsoft Intune
Subscribe to get the latest posts sent to your email.




Hi Peter,
thanks for pointing me in the right direction – I was able to solve my problem yesterday, I was only missing the Authenticator config. I’m now stuck at the “Experiencing QR code authentication on Android apps” step. I can create a QR Code for my testuser, but once I scan it with the managed home screen, I get a “Wrong QR-Code. You cannot be logged in with this QR-Code. Please scan the QR-Code provided by your organization” (translated from German). Any idea on what this could be?
Best Regards
Manuel
Hi Manuel,
Just to be sure; that QR code belongs to the user and the user and device are in the same tenant? If so, do you see the sign in of the user in the logging?
Regards, Peter
Hi Peter,
yes, QR code belongs to the user (I’m right at the entra authentication methods page) and also yes to the same tenant. There was nothing in the sign-in logs, which considering the error message doesn’t suprise me, as it didn’t really try to login and just rejected the QR code outright.
Hi Manuel,
Once QR code authentication is allowed and the Authenticator app is configured, there is not a lot more that can be configured. Can you reproduce that behavior for multiple users and on different devices?
Regards, Peter
The funny thing: I tried it yesterday with the same user, same test device – and it worked. Tested around some more and found I still get the same error, when using the “emergency qr code” you can generate should the user not have access to his usual qr code.
But I hopefully won’t need that. Now I need to find out if I can make things more streamlined – authenticator is asking every time if it can use the camera which is kind of annoying. Also Teams always asks if I want to logout on first start – and only logs in once I logout. I would have assumed the logout would happen automatically here on a shared device?
Hi Manuel,
Good to hear that it’s working now. For Shared Device Mode supported apps, the sign-out should happen automatically when signing out of the device. See also: https://learn.microsoft.com/en-us/entra/identity-platform/msal-shared-devices
Regards, Peter
Hi Peter, I followed your guide but the Configuration Policy does not apply to the device.
Any idea?
Do I might need a App Protection Policy in place to make the assignment happen?
Looking forward!
Regards,
Sebastian
Hi Sebastian,
Depends on the type of management. But on managed devices that should not be necessary. See also: https://learn.microsoft.com/en-us/intune/intune-service/apps/app-configuration-policies-overview#apps-that-support-app-configuration
Regards, Peter
Hello Peter,
Thank you very much for your instructions!
Unfortunately, I get a pop-up every time I want to scan a QR code to allow camera access.
I have already set the camera permission for the authenticator to “Auto grant” via an app config.
Nevertheless, the pop-up appears every time I want to scan a QR code.
Is there a way to prevent this?
Greetings
Simon
Hi Simon,
Yes, I’ve seen the same behavior, but I’ve not really looked at it in much detail yet. Is it the Authenticator that is prompting or the app that is asking for the QR code sign-in?
Regards, Peter
I do think it is the Authenticator App that is asking. I have found no Intune Policy to grant these permissions (or the ones for the Managed Home Screen). It looks like this is only possible via OEMConfig of the DeviceVendor. Which in my case is not possible, as our device vendor does not support it.
It would be great if the Authenticator App could atleast “save” the camera permission once you granted it. Asking each and every time is kind of cumbersome.
Totally agree on that assessment Manuel.
Regards, Peter
Since we have set the authenticator to “preffered authentication method qrpin”, I assume that it is the authenticator that asks for the camera access when we try to sign in…
Thank you for that Simon.
Regards, Peter