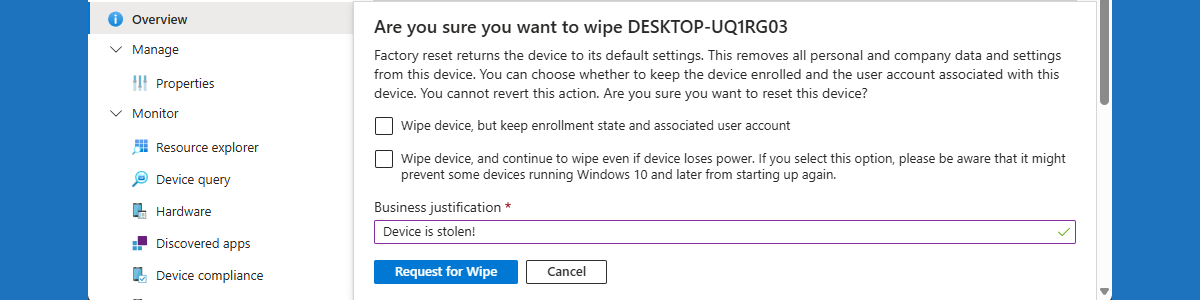
Preventing accidental device wipe with multiple administrative approval in Microsoft Intune
This week is all about the preventing accidental device wipes by using multiple administrative approval in Microsoft Intune. Multiple administrative approval on itself is nothing new, but the latest addition to that functionality makes it a lot more powerful. Before, multiple administrative approval was mainly focused adding apps and scripts to Microsoft Intune. Nowadays, multiple administrative approval can also be used for Intune roles and the most critical device actions. Those device actions include device wipe, device retire, and device delete. With those device actions, there will be a little safety net for IT administrators when performing impactful device actions without really giving in on security. Multiple administrative approval will help with preventing accidentally wiping a device. Every device wipe will require an approval from …