This week is all about getting started with the Global Secure Access client for Android. That makes this post a follow-up on this post about getting started with the Global Secure Access client for Windows of a few months ago. To start with a similar short introduction, Global Secure Access is the Security Service Edge (SSE) solution of Microsoft. Gartner defines SSE as a solution that secures access to the web, cloud services and private applications, regardless of the location of the user or the device they are using or where that application is hosted. Within Global Secure Access, Microsoft introduced Entra Internet Access and Entra Private Access to provide that functionality. Of those products, Entra Internet Access is focused on secured access to Microsoft 365, SaaS, and public apps, while Entra Private Access is focused on secured access to private or internal resources. The Global Secure Access client can be used to connect to the Global Secure Access solution. On Android devices that client is part of the Microsoft Defender for Endpoint app. This post will focus on deploying that app on Android devices and making sure that the app is correctly configured for Global Secure Access. This post will end with the user experience.
Note: Entra Internet Access and Entra Private Access are part of the Microsoft Entra Suite license or standalone.
Deploying the Microsoft Defender: Antivirus app
When specifically looking at the deployment of the Global Secure Access client for Android, the process is pretty straightforward via Microsoft Intune. Pretty similar actually to deploying any other Android app. That process relies on the Managed Google Play Store. It is, however, good to understand the app that should be deployed. The Global Secure Access client is part of the Microsoft Defender for Endpoint, also known as Microsoft Defender: Antivirus. The following six steps walk through the process of adding the Microsoft Defender: Antivirus app to Microsoft Intune and deploying it to the required users.
- Open the Microsoft Intune admin center portal navigate to Apps > Android
- On the Android | Android apps page, click Add > Managed Google Play app and click Select
- On the Managed Google Play page, search and select Microsoft Defender: Antivirus
- On the Microsoft Defender: Antivirus page, as shown below in Figure 1, click Select (1) and click Sync (2)

- Back on the Android | Android apps page, select Microsoft Defender: Antivirus > Properties
- On the Microsoft Defender: Antivirus | Properties page, click Edit with the Assignments section, configure the required assignment for the app and click Review + Save
Configuring the Microsoft Defender: Antivirus app
After the Microsoft Defender: Antivirus app has been added to Microsoft Intune, the app must be configured to enable Global Secure Access and eventually also Entra Private Access. To make those configuration changes, an app configuration policy can be used. That policy can be used to specify the required configuration keys to enable Global Secure Access (Global Secure Access) and Entra Private Access (GlobalSecureAccessPA). The following six steps walk through the process of adding the app configuration policy for enabling Global Secure Access via the Microsoft Defender: Antivirus app.
- Open the Microsoft Intune admin center portal navigate to Apps > Android > Configuration
- On the Android | Configuration blade, click Create > Managed devices
- On the Basics page, provide the following information and click Next
- Name: Provide a unique name to distinguish it from similar profiles
- Description: (Optional) Provide a description to further distinguish it from similar profiles
- Device enrollment type: (Grayed out) Managed devices
- Platform: Select Android Enterprise as the platform
- Profile Type: Select Fully Managed, Dedicated, and Corporate-Owned Work Profile Only as profile type
- Targeted app: Select Microsoft Defender: Antivirus as the targeted app
- On the Settings page, provide at least the following information and click Next
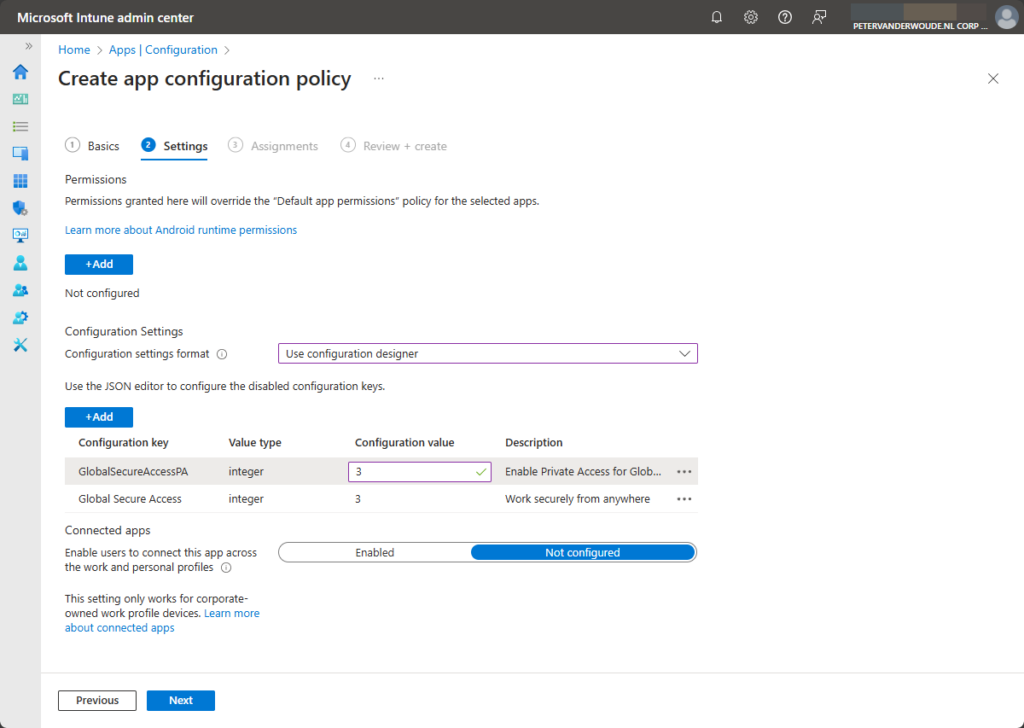
- On the Configuration settings section, as shown below in Figure 2, perform at least the following actions
- Configuration settings format: Select Use configuration designer
- Click Add to add the Global Secure Access and the GlobalSecureAccessPA configuration key
- Select integer as value type for both setting and specify 2 as the configuration value for both settings to make sure that Private Access toggle is visible and defaults to enabled state and that the Global Secure Access tile is visible and defaults to enabled state.
- On the Assignments page, configure the required assignment by selecting the applicable user group and click Next
- On the Review + create page, review the configuration and click Create
Note: Keep in mind that this configuration can also be used in combination with other app configurations.
Experiencing Global Secure Access
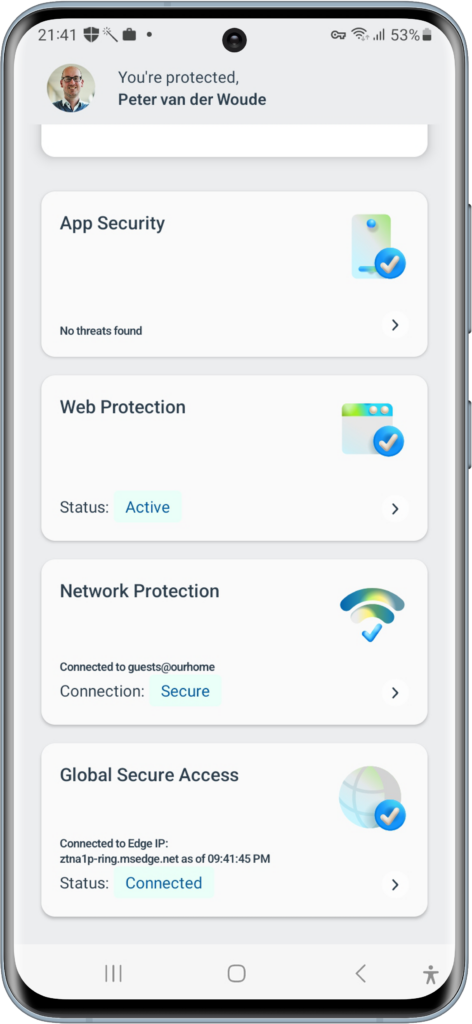
After the Microsoft Defender: Antivirus app is deployed and configured, it’s pretty straight forward to experience the behavior of Global Secure Access. Simply open the Microsoft Defender: Antivirus app and scroll down to the section Global Secure Access, as shown below in Figure 3. That already provides a brief overview of the current status. Now tap on Global Secure Access to get the ability to turn it off, as shown below in Figure 4, and to learn more about the solution. To get an overview of the connected services, simply tap on Services, as shown below in Figure 5. That clearly shows the state of the different services, including a slider with the Private Access service.
More information
For more information about the Global Secure Access client for Windows, refer to the following docs.
- Learn about the Global Secure Access clients for Microsoft Entra Private Access and Microsoft Entra Internet Access – Global Secure Access | Microsoft Learn
- The Global Secure Access Client for Android – Global Secure Access | Microsoft Learn
Discover more from All about Microsoft Intune
Subscribe to get the latest posts sent to your email.




Have you managed to get this working with app protection policies along with a conditional access policy?
I can’t seem to get defender to sign in unless I exclude the defender app on the CA policy. But once signed in, I keep getting prompts to sign to GSA. Looks like it is not compatible with CA policies.
Hi Bojack,
You might want to look at this: https://learn.microsoft.com/en-us/defender-endpoint/mobile-resources-defender-endpoint#microsoft-defender-mobile-app-exclusion-from-conditional-access-ca-policies
Regards, Peter