This week is all about enabling optional Windows updates. Enabling optional updates is all related to the Get the latest updates as soon as they’re available slider in the Settings app. That slider can be used to enable optional updates on a Windows device. Optional updates provide new features and non-security changes. Besides that, optional updates can also include features that are gradually rolled out. Those rollouts are also known as controlled feature rollouts (CFRs). Most of those optional updates are released on the fourth Tuesday of the month and are also known as non-security preview releases, while regular updates are released on the second Tuesday of the month. Nowadays, regular updates are also known as B week releases, while optional updates are also known as D week releases. By default, the installation of optional updates isn’t enabled for devices that rely on Window Update for Business. This post will have a closer look at the configuration options for enabling optional updates, followed with the steps for configuring those options. This post will end with the user experience with optional updates enabled.
Configuring optional updates
When looking at configuring the ability to enable optional Windows updates, it all starts with the configuration options. The Policy CSP contains the Update area. That area contains all the settings to manage updates that are delivered via Windows Update. Many of those settings are ADMX-backed settings, including the setting to enable optional updates. That setting is AllowOptionalContent and is backed by the WindowsUpdate.admx. It can be configured to multiple values that all create a different user experience. And that’s also directly the link with the Get the latest updates as soon as they’re available slider in the Settings app. The configuration of that setting reflects to the status of the slider and the available values are described below.
| Value | Description | Experience |
|---|---|---|
| 0 | (Default) Don’t receive optional updates | Optional non-security updates are not installed on the device. The Get the latest updates as soon as they’re available option is not selected and the user can change the setting. |
| 1 | Automatically receive optional updates (including CFRs) | Optional non-security updates and CFRs are automatically installed on the device. The Get the latest updates as soon as they’re available option is selected and users cannot change the setting. |
| 2 | Automatically receive optional updates | Optional non-security updates are automatically installed on the device, but CFRs are not. The Get the latest updates as soon as they’re available option is not selected and users cannot change the setting. |
| 3 | Users can select which optional updates to receive | Optional non-security updates are offered to the device, but user interaction is required to install them unless the Get the latest updates as soon as they’re available option is selected by the user. |
Note: When enabling optional updates, the setting still respects the deferral period for quality updates.
At this moment this specific setting is not yet available within the Settings Catalog, which is the reason to fallback to a Custom configuration profile. That enables the configuration of any available CSP setting in Windows. The following nine steps walk through the configuration of enabling optional updates on Windows devices.
- Open the Microsoft Intune admin center navigate to Devices > Windows > Configuration profiles
- On the Windows | Configuration profiles blade, click Create > New policy to open the Create a profile page
- On the Create a profile page, provide the following information and click Create
- Platform: Select Windows 10 and later as value
- Profile type: Select Templates as value
- Template name: Select Custom as value
- On the Basics page, provide a unique Name to distinguish the profile from other custom profiles and click Next
- On the Configuration settings page, as shown below in Figure 1, click Add to add the following row and click Next
- OMA-URI setting (1) – This setting is used to enable optional updates
- Name: Provide a name for the OMA-URI setting to distinguish it from other similar settings
- Description: (Optional) Provide a description for the OMA-URI setting to further differentiate settings
- OMA-URI: Specify ./Device/Vendor/MSFT/Policy/Config/Update/AllowOptionalContent
- Data type: Select Integer as value
- Value: Specify 1 as value

- On the Scope tags page, configure the applicable scopes and click Next
- On the Assignments page, configure the assignment and click Next
- On the Applicability rules page, configure any required applicability rules and click Next
- On the Review + create page, verify the configuration and click Create
Note: The setting for enabling optional updates will come over time to the Settings Catalog.
Experiencing enabled optional updates
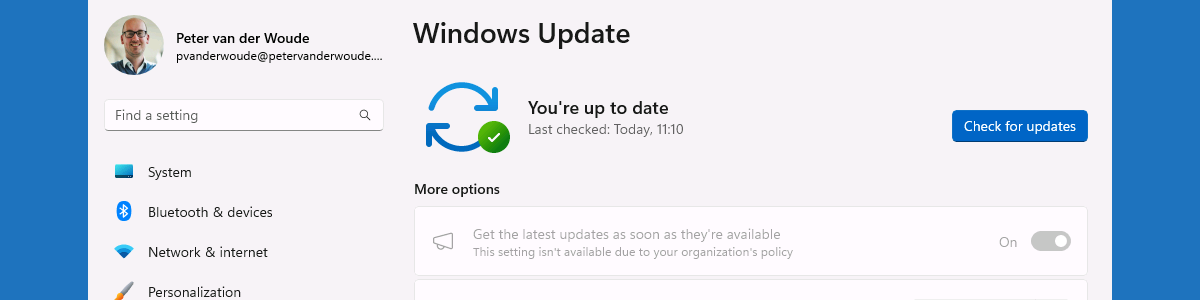
After applying the configuration for enabling optional updates, it’s pretty straight forward to verify and experience that configuration. To verify the configuration, simply open the Settings app and navigate to Windows Update. That contains the relatively new setting Get the latest updates as soon as they’re available. With the example configuration of this post that setting should be grayed out and set to On, as shown below in Figure 2, to configure the Windows device to automatically receive optional updates (including CFRs). After enabling the configuration, it still respects the deferral period for quality updates. That configuration could be useful to make sure that at least a specific group of users can test the impact of new non-security updates, before those updates get into production a few weeks later. Of course, the opposite configuration could also be very useful. There will always be specific devices within the environment that should not get those type updates before they’re tested within the environment.

More information
For more information regarding Windows Update for Business configuration options, refer to the following docs.
Discover more from All about Microsoft Intune
Subscribe to get the latest posts sent to your email.

FYI, it’s in the Settings Catalog. Allow Optional Content
Thank you for that Coert! It wasn’t when I was writing the post, or I must have been really blind…
Regards, Peter
Is there a way to install Optional Updates but NOT the preview updates?
Hi RDP,
This specific setting can only be used in the different status as provided in this post. And those settings are focussed on the preview updates.
Regards, Peter
thanks. I was wondering how to push non-security updates via Intune