This week another blog post focused on the security capabilities within Microsoft Edge. With the introduction of Microsoft Edge for Business, there is a larger focus on providing a Microsoft Edge experience for work. That experience provides IT administrators with the ability to give their users a productive and secure browser for work, across managed and unmanaged devices. With that, Microsoft Edge can be the secure enterprise browser for many organizations. Especially with the focus of Microsoft Edge on security, privacy, and manageability. And not just that, it includes enhanced productivity alongside the security features. That brings us to the focus of this week and that is in-browser protection. In-browser protection is a great example of that combination as it reduces the need for proxies, improving both security and productivity. This post will start with a brief introduction about in-browser protection in Microsoft Edge, followed with the configuration and the user experience.
Important: At the moment of writing, in-browser protection in Microsoft Edge for Business is still in preview.
Introducing in-browser protection in Microsoft Edge
When using Microsoft Defender for Cloud Apps in combination with Microsoft Edge, the user experience can be made a whole friendlier for session policies. That experience makes sure that users are protected directly from within the browser. In-browser protection reduces the need for proxies, improving both security and productivity. Protected users experience a smooth experience with their cloud apps, without latency or app compatibility issues, and with a higher level of security protection. For that smooth experience the users must be in their work profile in their browser. Microsoft Edge profiles allow the users to split browsing data into separate profiles. That makes sure that the data that belongs to each profile is kept separate from the other profiles. In combination with mobile application management (MAM) that separate work profile is also protected on the device.
For in-browser protection to work, it is important that only supported session policies are being used. When users are served by at least one policy that’s not supported by Microsoft Edge, their sessions are served by the reverse proxy. That is also applicable to policies that are directly defined in Conditional Access policies in the Microsoft Entra ID portal. The following configurations are supported in session policies for in-browser protection Microsoft Edge:
- Block (or monitor) file download (all files/sensitive files)
- Block (or monitor) file upload (all files/sensitive files)
- Block (or monitor) copy/cut/paste
- Block (or monitor) print
- Block (or monitor) malware upload
- Block (or monitor) malware download
Note: Combining other settings with the supported policies result in sessions that are served by the reverse proxy.
Configuring in-browser protection in Microsoft Edge
After being familiar with in-browser protection in Microsoft Edge, and the different supported policies, it’s time to look at actually configuring it by using Microsoft Defender for Cloud Apps. The good news is that in-browser protection is nowadays enabled by default. That means that the configuration is only required to enforce the usage of Microsoft Edge, or to actually disable in-browser protection. The configuration is pretty straight forward and available via the Microsoft Defender portal. The following 2 steps can be used to enable in-browser protection and the enforce the use of Microsoft Edge.
- Open the Microsoft Defender portal and navigate to Setting > Cloud Apps`> Conditional Access App Control section > Edge for Business protection
- On the Edge for Business protection page, as shown below in Figure 1, make sure that the following settings are in place and click Save
- Turn on Edge for Business browser protection (1): Make sure that the slider is switched to the right to turn on in-browser protection in Microsoft Edge for Business
- Enforce usage of Edge for Business (2): Select Allow access only for Edge to enforce the use of Microsoft Edge for Business
- Enforce for which devices? (3): Select All devices to enforce Microsoft Edge for Business on all devices
- Check Notify users in non-Edge browsers to use Microsoft Edge for Business for better performance and security (4) to notify users to Edge and choose the message template to use
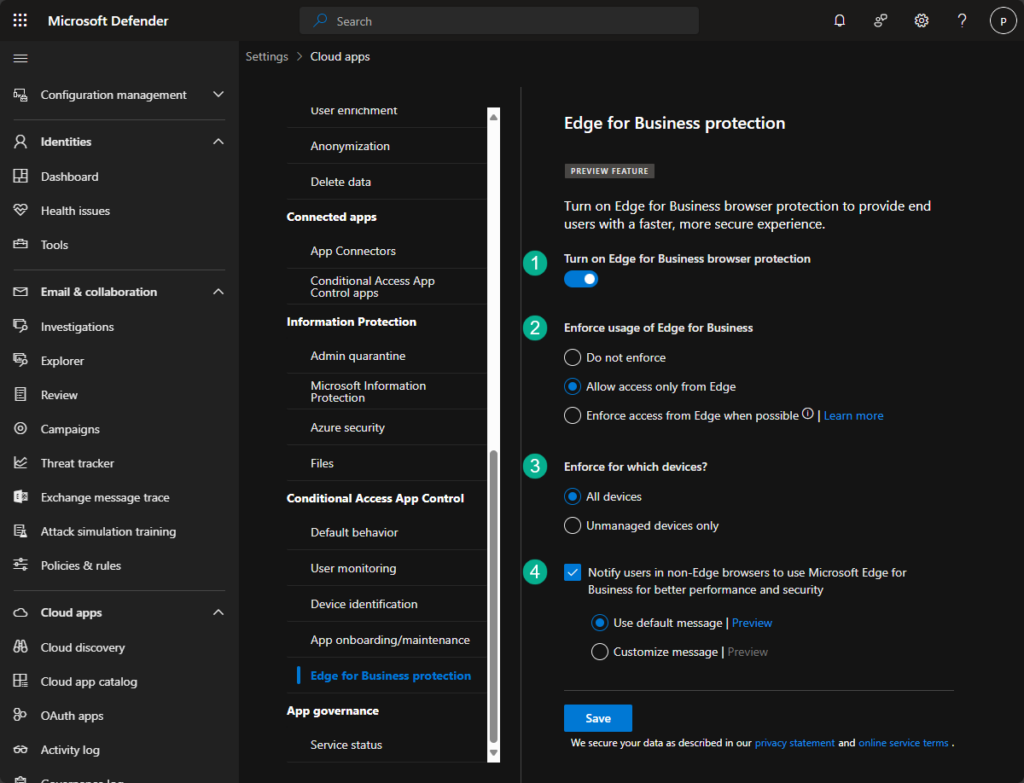
Note: The option Enforce access from Edge when possible is the more friendly method for enforcing Microsoft Edge for Business. In that case users should use Microsoft Edge to access the application if their context permits.
Experiencing in-browser protection in Microsoft Edge
When the configuration for in-browser protection is in place, and a supported session policy is configured, it’s time to look at the user experience. That experience is pretty straight forward to verify by simply navigating to a work resource. When trying that from outside Microsoft Edge, the user will be prompted to use Microsoft Edge. And when trying that from outside the work profile, the user will be prompted to switch to the work profile. When navigating to a work resource, such as portal.office.com, for the work profile in Microsoft Edge, the user can experience the in-browser protection. Below in Figure 2 and Figure 3 are overviews of how to verify that experience. Simply click on the “lock” icon and look for the “suitcase” icon with Defender for Cloud Apps (Figure 2), as that is the indication that in-browser protection is enabled. Besides that, performing any of the supported actions, such as trying to copy data, the user will receive an in-browser notification that the action is blocked (Figure 3).


More information
For more information about tightening Microsoft Edge browser security, refer to the following docs.
- Microsoft Edge for Business Recommended Configuration Settings | Microsoft Learn
- In-browser protection with Microsoft Edge for Business – Microsoft Defender for Cloud Apps | Microsoft Learn
Discover more from All about Microsoft Intune
Subscribe to get the latest posts sent to your email.


1 thought on “Working with in-browser protection in Microsoft Edge for Business”